
A critical Chrome zero-day was exploited by hackers backed by North Korea in an attempt to steal information from hundreds of people working in a wide range of industries.
Two separate North Korean hacking groups exploited the flaw. Both groups used the same exploit kit on websites that were either hacked or were set up for the express purpose of serving attack code on visitors. More than 250 people were targeted by the group dubbed Operation Dream Job. The other group targeted 85 users.
We suspect that these groups work for the same entity with a shared supply chain, but each operate with a different mission set and deploy different techniques.
Researchers at ClearSky observed a group targeting defense and governmental companies in June 2020. The bad guys targeted specific employees in the organizations with fake offers of jobs at companies such as Boeing. The hackers created an elaborate social-engineering campaign that used fake profiles, emails, and phone calls. The goal of the campaign was to steal money.
AppleJeus, meanwhile, dates back to at least 2018. That's when researchers from security firm Kaspersky saw North Korean hackers targeting a cryptocurrency exchange using malware that posed as a cryptocurrency trading application. The AppleJeus operation was notable for its use of a malicious app that was written for macOS, which company researchers said was probably the first time an APT—short for government-backed "advanced persistent threat group"—used malware to target that platform. Also noteworthy was the group's use of malware that ran solely in memory without writing a file to the hard drive, an advanced feature that makes detection much harder. Advertisement One of the two groups (Weidemann didn't say which one) also used some of the same control servers to infect security researchers last year. The campaign used fictitious Twitter personas to develop relationships with the researchers. Once a level of trust was established, the hackers used either an Internet Explorer zero-day or a malicious Visual Studio project that purportedly contained source code for a proof-of-concept exploit.A critical vulnerability was discovered in the browser in February. The vulnerability was fixed by company engineers. The company gave more information about how the two North Korean hackers were able to exploit the vulnerability.
The emails that were sent to targets were supposedly from recruiters for Disney and other companies. The links in the email spoofed legitimate job hunting sites. The exploit was triggered by an iframe on the sites.
Here is an example of a page.
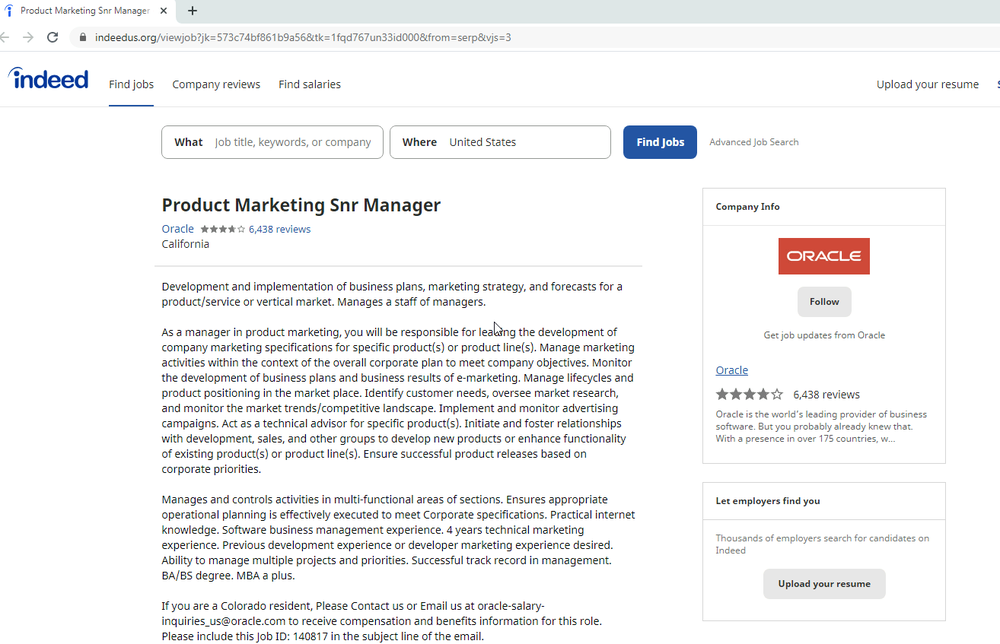
At least two legitimate financial services companies and a variety of ad hoc sites were compromised by members of Apple Jeus. The Dream Job sites contained iframes that triggered the exploit.
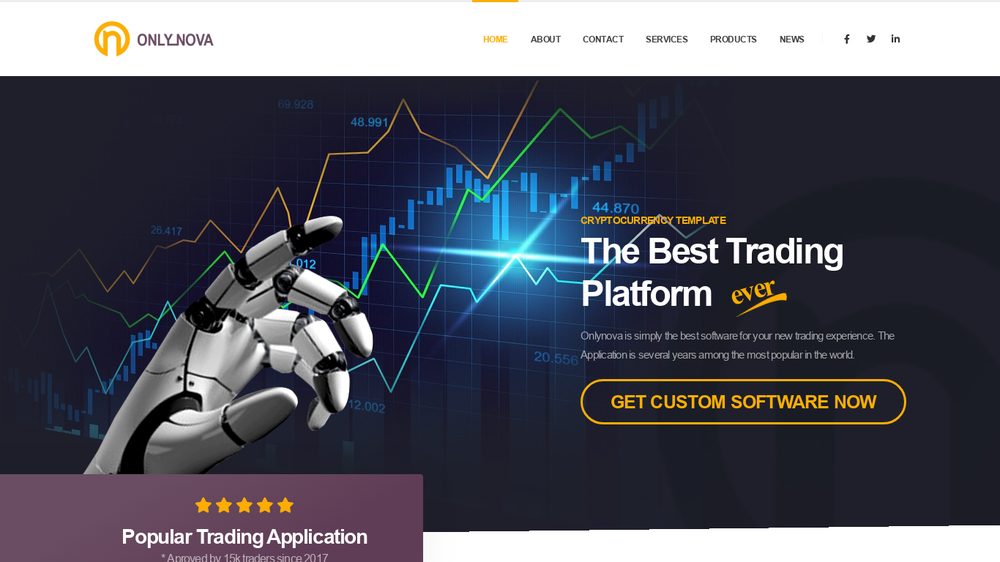
The exploit kit was written in a way to hide the attack by disguising the exploit code and triggering remote code execution only in select cases. The kit appears to have used a separate exploit to break out of the Chrome security sandbox. The vulnerability it exploited has yet to be patched, even though the researchers were unable to determine that escape code.