
When we teach people how to avoid falling victim to phish sites, we usually advise them to inspect the address bar to make sure it doesn't contain suspicious domain names or substitute letters. If someone found a way to phish passwords using a malicious site that didn't contain telltale signs, what would happen?
A researcher has come up with a way to do that. He calls it a BitB, short for Browser in the Browser, and it uses a fake browser window to spoof an OAuth page. Hundreds of thousands of websites use the OAuth protocol to allow visitors to use their existing accounts with companies like Apple. Visitors can use an account that they already have, and the magic of OAuth, instead of having to create an account on the new site.
Visitors to the photo editing site can use any of three common accounts to log in. The images below show what a user sees after clicking the sign in button, followed by the image showing what appears after signing in with a password. A new browser window with a legitimate address opens in front of the existing Canva window after the user chooses a search engine.
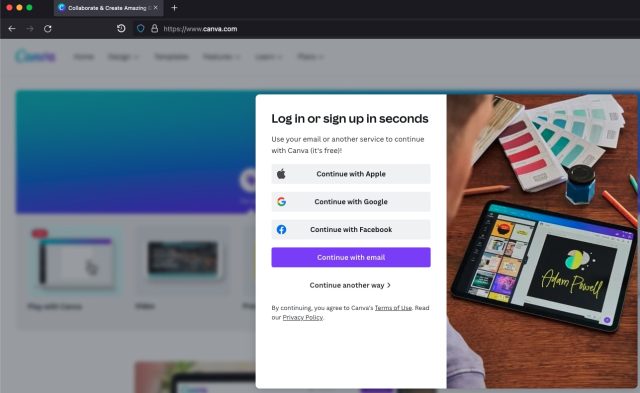
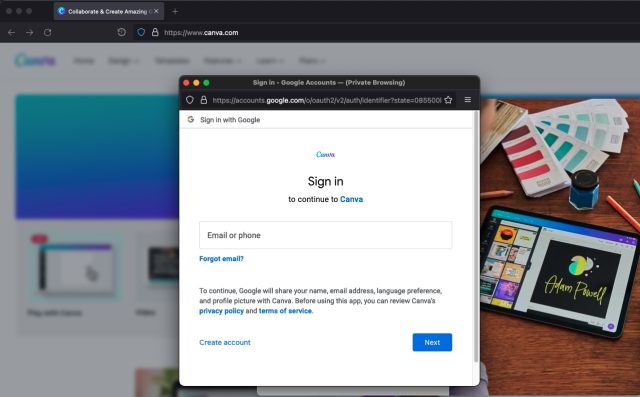
The user's password is only received by Google. Canva doesn't see the credentials. When the visitor checks out with their password and usernames, they will be provided with a token that will allow them to use Canva. When a shopper chooses a payment method, there is something similar.
Advertisement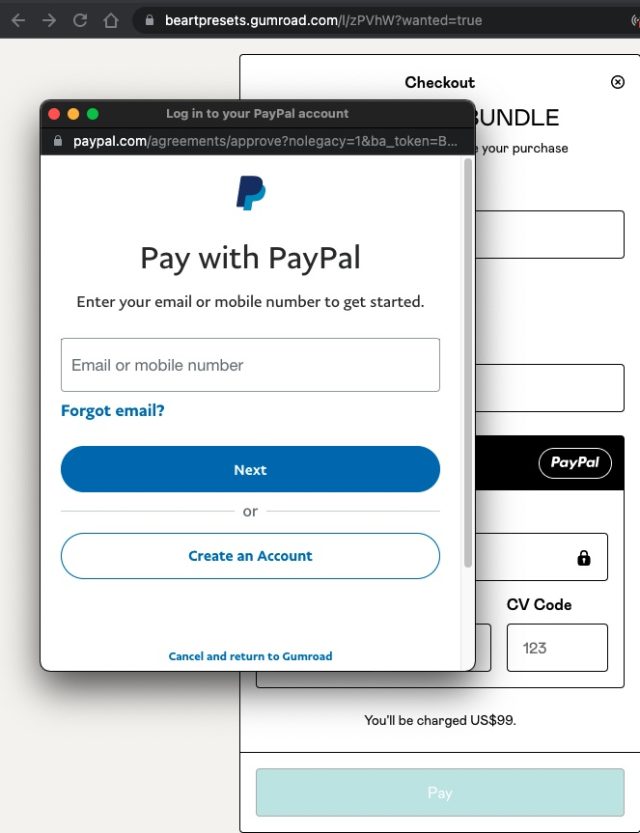
This scheme is capitalized by the BitB technique. BitB uses a series of tricks to spoof the second window, which is connected to the site to facilitate the login or payment. A valid address can be found in the URL that appears. The layout and behavior of the window are the same as the real thing.
A researcher described the technique last week. The proof-of-concept exploit begins on a Web page. The fake Canva page opens a new page that looks similar to the OAuth page if a visitor chooses to use Apple, Facebook, or Google.

The new page is a spoof. A person would expect to see all the graphics when using the internet. The address bar on the page appears to be a legitimate one. The new window behaves like a browser window if connected to a real OAuth session.
If a potential victim opens the fake Canva.com page, it will open a new browser window and take them to the URL accounts ofgoogle.com. The fake Canva site doesn't open a new browser window. It looks like a new browser window, but it's only a text book. The fake window sets the URL to accounts.google.com.
A security researcher created a video that shows what the technique looks like after watching the demonstration. It explains how easy it is to do it.
AdvertisementIt is surprising that the BitB technique is not better known. After Mr.d0x wrote about the technique, a small group of researchers remarked how likely it would be for more experienced users to fall for it.
One developer wrote that this browser-in-the-browser attack is perfect for phishers. We do not want to give you ideas.
Another person said that Browser In The Browser (BITB) Attack is a new technique that allows stealing credentials that even a web professional can't detect.