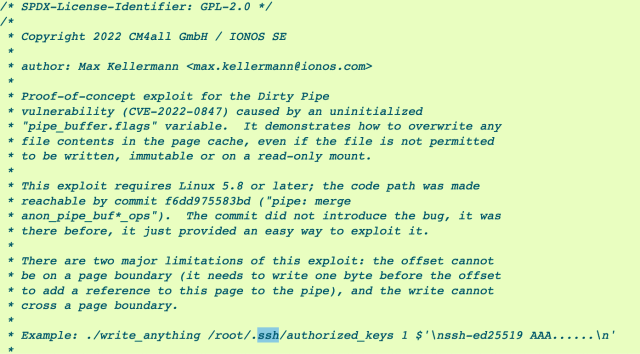
Linux has a number of vulnerabilities that make it easy for users to execute code that can be used to carry out a host of malicious actions, including installing backdoors, creating unauthorized user accounts, and modifying script or binaries used by privileged services or apps. The name Dirty Pipe is meant to signal similarities to Dirty Cow and provide clues about the vulnerability&s origins. The output text of one process is passed directly as input to the next process in a pipeline. The vulnerability was discovered when a researcher for website builder CM4all found corrupted files on a customer's Linux machine. The researcher found a bug in the Linux kernel that caused the corrupted files. The researcher at CM4all eventually figured out how to weaponize the vulnerability to allow anyone with an account. With that, the user with full root privileges could access the server with an ssh window. The unauthorized creation of an SSH key was one of many malicious actions an attacker can take when exploiting the vulnerability. This program hijacks an SUID to create a root shell, while this one allows users to change data in read only files.
When Nobody becomes all powerful
Adding a new user account to /etc/passwd is one of the malicious actions enabled by Dirty Pipe.
Brad Spengler, president of Open Source Security, wrote in an email that it was as severe as a local vulnerability.
The vulnerability first appeared in the Linux kernel version 5.8. The vulnerability was fixed last month with the release of versions 5.16.11, 5.15.25 and 5.10. All distributions of Linux are affected.
Dirty Pipe can affect any release of Android that is based on a vulnerable Linux version. The affected device models can not be tracked in a uniform way. The latest version of the operating system for the phones is 5.10.43, meaning they are vulnerable. The 4.14 operating system for the Pixel 4 is unaffected. If you want to know which version your device uses, you can go to the settings.
The Dirty Pipe vulnerability is extremely serious in that it allows an attacker to permanently change the system's files.
The vulnerability can be exploited through a malicious app that raises its privileges, which is supposed to be limited, according to the Lookout researcher. Another way of attacking is to use a different exploit to gain limited code execution and combine it with Dirty Pipe so the code gains unfettered root.
There are no indications that the vulnerable version of the Linux kernel is fixed, despite Kellermann's claim that a bug fix was merged with the Android kernels in February. Users should assume that any device running a version of Android that has a vulnerable version of the Linux kernel is vulnerable to Dirty Pipe. An email seeking comment was not responded to.