
Last August, academic researchers discovered a potent new method for knocking sites offline: a fleet of misconfigured server more than 100,000 strong that can amplify floods of junk data to once-unthinkable sizes. In many cases, these attacks could result in a flood of traffic. The attackers are exploiting the server to target sites in the banking, travel, gaming, media, and web-hosting industries.
China uses middleboxes to censor restricted content and large organizations block sites that push porn, gambling, and piracy. The server fails to follow transmission control protocol specifications that require a three-way handshake, SYN+ACK response from the server, and a confirmation ACK packet from the client before a connection is made.
The ACK confirmation must come from the gaming company or other target rather than an attacker spoofing the target's IP address to be able to abuse the app. The middlebox can monitor packets delivered from the client but not the final destination that is being blocked, which is why many server drop the requirement.
In August of last year, researchers at the University of Maryland and the University of Colorado at Boulder published research showing that there were hundreds of thousands of middleboxes that could deliver some of the most devastating distributed denial of service attacks ever seen.
For decades, people have used distributed denial of service (DDoS) to flood websites with more traffic than they can handle. The old prank of directing more calls to the pizza parlor than the phone lines can handle was similar to the current prank of directing more calls to the pizza parlor than the phone lines can handle.
AdvertisementTo maximize the damage and conserve resources, the amplification of their attacks is increased. Amplification works by spoofing the target's IP address and bouncing a relatively small amount of data to a misconfigured server used for resolving domain names,sync computer clocks, or speeding up database caching. The spoofed target is overwhelmed by the response the server automatically sends.
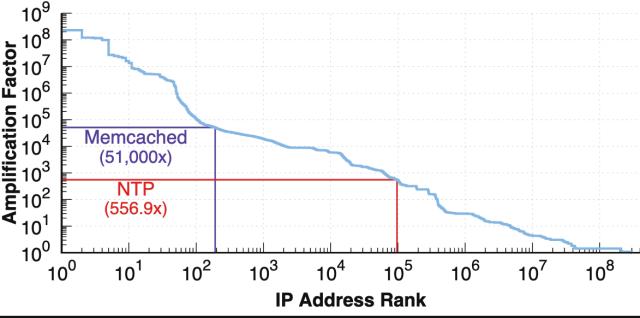
The researchers said that at least 100,000 of the middleboxes they identified exceeded amplification factors. The researchers said that they identified hundreds of server that amplified traffic at a higher multiplier than the rest of the network, which can increase traffic volume by 51,000x.
Here is an overview of how the attacks work.
It would only be a matter of time before middlebox amplification attacks were used actively in the wild, the researchers said at the time.
On Tuesday, researchers at Akamai said that day had come. Over the past week, the researchers at Akamai have detected multiple attacks that used middleboxes exactly as they were predicted. 1.5 million packets per second were the peak of the attacks.
While small when compared to the biggest DDoSes, both teams of researchers expect the attacks to get larger as DDoSers begin to optimize their attacks and identify more middleboxes that can be abused (the academic researchers didn’t release that data to prevent it from being abused).Kevin Bock, the lead researcher behind last August's research paper, said there were plenty of incentives to reproduce the attacks his team theorize.
AdvertisementHe told me that they were not surprised when they learned of the active attacks. The attacks are new and many operators don't have defenses in place, which makes it more attractive to attackers.
One of the middleboxes received a SYN packet and responded with a 2,156-byte reply.
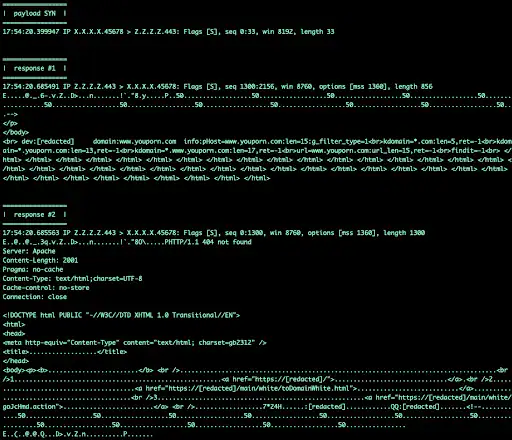
The amplification has the potential to be much greater with more work.
Researchers from Akamai wrote.
Volumetric TCP attacks previously required an attacker to have access to a lot of machines and a lot of bandwidth, normally an arena reserved for very beefy machines with high-bandwidth connections and source spoofing capabilities or botnets. This is because until now there wasn’t a significant amplification attack for the TCP protocol; a small amount of amplification was possible, but it was considered almost negligible, or at the very least subpar and ineffectual when compared with the UDP alternatives.
If you wanted to marry a SYN flood with a volumetric attack, you would need to push a 1:1 ratio of bandwidth out to the victim, usually in the form of padded SYN packets. With the arrival of middlebox amplification, this long-held understanding of TCP attacks is no longer true. Now an attacker needs as little as 1/75th (in some cases) the amount of bandwidth from a volumetric standpoint, and because of quirks with some middlebox implementations, attackers get a SYN, ACK, or PSH+ACK flood for free.