
Home and small-office network devices around the world have been compromised by hackers from one of Russia's most elite and brazen spy agencies, who have turned them into attack platforms that can steal confidential data and target other networks.
According to the company, about 1 percent of network firewall devices made by Watchguard have been affected by the advanced malware. The software is able to abuse a legitimate update mechanism found in the devices that it is installed on.
Sandworm hackers built a new piece of software after the exposure of VPNFilter. The same as its predecessor, Cyclops Blink has all the trappings of professionally developed firmware, but it also has new tricks that make it stealthier and harder to eradicate.
Officials with the UK's National Cyber Security Center wrote in an advisory that the software itself is sophisticated and modular with basic core functions to beacon device information back to a server and enable files to be downloaded and executed.
AdvertisementThe advisory stated that Sandworm used the software to get into network devices from WatchGuard, but it's likely the hackers are able to build it for other platforms as well. The WatchGuard devices have a legitimate process that they use to receive updates.
The malicious software starts by copying the images on the device. The HMAC value is used to prove the image is legitimate so devices will run it. The process looks similar.
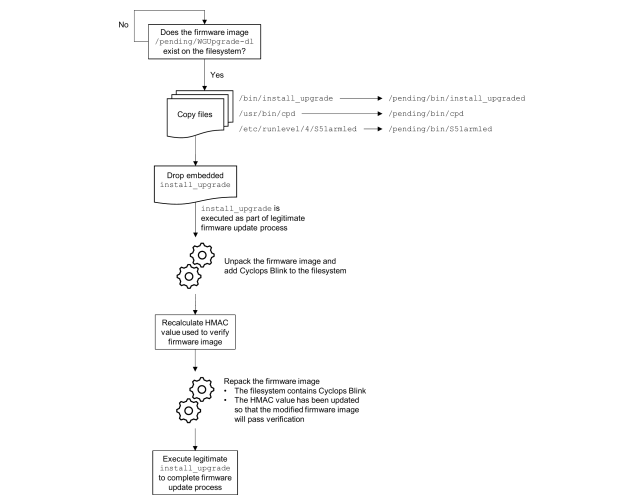
The samples analyzed by the UK officials don't appear to have used the hard-coded RSA public key or the hard-coded RSA private key in any way.
The OpenSSL library is used to protect communications.
The advisory stated that the malware randomly selects a destination from the current list of C2 server IPv4 addresses and hard-coded list of C2 ports. Each message is ciphered using a special program. The OpenSSL_EVP_SealInit function uses a hard-coded RSA public key to generate the encryption key and IV for each message. The hard-coded RSA public key is used in the OpenSSL_RSA_public_decrypt function.
New stealth measures include using the Tor privacy network to hide the addresses of the malware. UK officials wrote.
AdvertisementVictim devices are organised into clusters and each deployment of Cyclops Blink has a list of command and control (C2) IP addresses and ports that it uses (T1008). All the known C2 IP addresses to date have been used by compromised WatchGuard firewall devices. Communications between Cyclops Blink clients and servers are protected under Transport Layer Security (TLS) (T1071.001), using individually generated keys and certificates. Sandworm manages Cyclops Blink by connecting to the C2 layer through the Tor network:
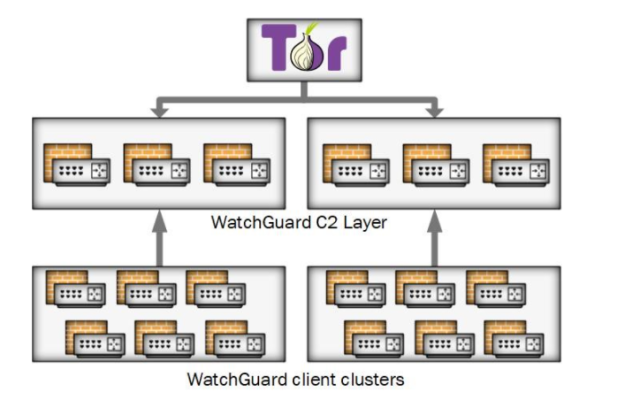
Mandiant was retained by WatchGuard to investigate the infections, as well as work with law enforcement.
There is no evidence of data exfiltration from WatchGuard or its customers, and the company's appliances are not at risk if they were never used. A list of indicators WatchGuard customers can use to detect infections is included in the document.
Sandworm is among the world's most advanced and cutthroat cyberattacks have been behind for almost two decades. Examples include:
Sandworm is a book that chronicles the hacks and the tensions they exploit. According to Wednesday's advisory, there is a chance that Cyclops blink could cause a large number of devices to be affected.
The UK officials wrote that the deployment of Cyclops Blink appears indiscriminate and widespread.