A new study suggests that you have good reason to worry about the privacy of your data when you seek a computer or phone repair. It found that privacy violations occurred at least 50 percent of the time.
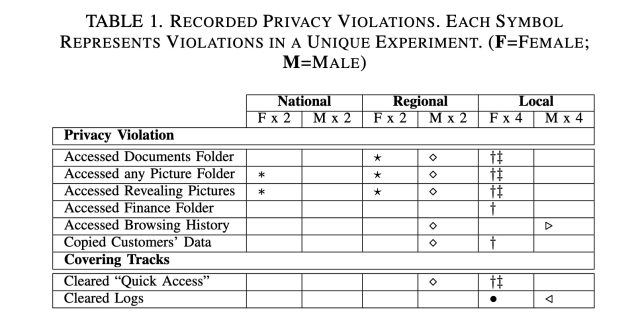
The logs from the laptops were recovered by the researchers at the University of Guelph. According to the logs, technicians from six of the locations accessed personal data and that two of them copied data onto a personal device. Devices belonging to females were more likely to be snooped on, and that snooping tends to seek more sensitive data, including both sexually revealing and non-sexual pictures.
One of the researchers said that they were blown away by the results. He was concerned about the copying of data during repairs for a male and female customer. They would just look at the data.
It is possible that the amount of snooping was higher than recorded in the study. The laptops were taken to 16 shops in the province. The logs from two of those visits weren't recovered. The technician had no chance to look at personal data when two of the repairs were performed on the spot.
AdvertisementThe researchers suspect that the snooping technician deleted the files in order to cover their tracks. The logs the researchers relied on being unrecoverable were the result of two of the visits. In another, the researcher said they had installed an anti-viruses software and performed a disk clean up. There was no explanation in the other case.
Six visits resulted in snooping.
Freshly imaged laptops are what the laptops were. The audio driver was disabled, but all were in perfect working condition. The researchers chose that glitch because it required only a simple and inexpensive repair, was easy to create, and didn't require access to users' personal files
Half of the laptops were configured to look like they belonged to a man and a woman. The laptops were all set up with email and gaming accounts. Sexually revealing and non-sexual pictures were added by the researchers.
The laptops were configured to run a logging app that used the Windows steps recorder utility. Each key pressed by the user was recorded by the utility. Windows Audit Policy was enabled by the researchers.
The laptops were brought to two national outlets and two regional outlets. Half of the customers were males and the other half were females.