Penn Engineering has created a chip that surpasses the security of existing quantum communications hardware. The quantum information space of any previous on-chip laser was doubled.
The Departments of Materials Science and Engineering (MSE) and Electrical Systems and Engineering ( ) have collaborated on a research project. Scientists from the Institute for Cross-Disciplinary Physics and Complex Systems, Duke University, and the City University of New York collaborated with the group.
There are bits and qubits.
State-of-the-art quantum devices use qubits. qubits are units of digital information that can be 1 and 0 at the same time. "superposition" is a term used in quantum mechanics.
A qudit is a quantum bit that is larger than two levels.
A pulse can be 1 or 0. They are not very secure because they are easy to clone and can be used to steal data. The pulse can have any position between 1 and 0. It is possible to copy a quantum pulse. A physical system that keeps information secure is called quantum Cryptography.
Qubits are imperfect. The qubits have limited storage space and low tolerance for interference.
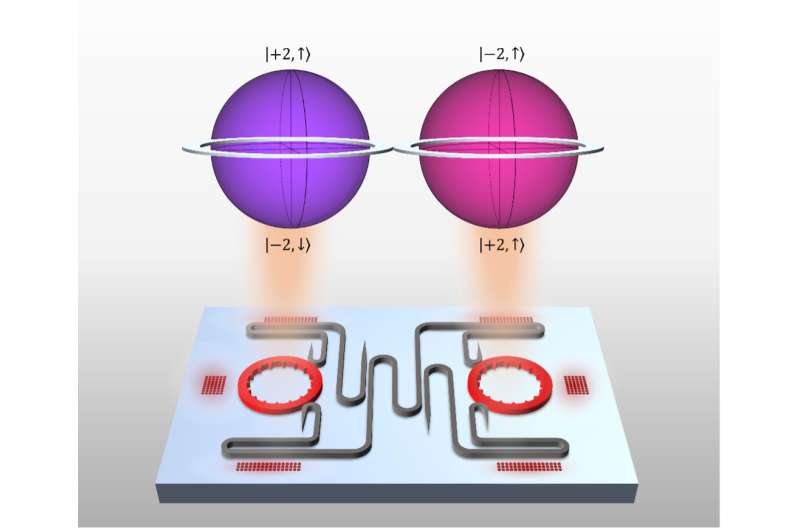
The maximum secret key rate for information exchange has been raised from 1 bit per pulse to 2 bits per pulse thanks to the four-level qudits. Four levels of superposition are offered by the device, which opens the door to more dimensions.
The standard setup was the biggest challenge. It required a lab and many different optical tools to control all the parameters associated with the increase in dimensions. We wanted to accomplish this on a single chip. We did that.
It's the physics of cybersecurity.
photons are used in quantum communication. There are properties at the quantum level that are governed by probabilities. The probability of a quantum system taking on a single attribute is described in these probabilities.
Quantum systems are not here or there. Both of them are here and there. A quantum system takes on a fixed property because of the act of observation. It's impossible to intercept quantum superpositions without detection or copying them because they take on a single state as soon as they're observed.
The hyperdimensional spin-orbit microlaser builds on the team's earlier work with vortex microlasers. The previous laser's capabilities were upgraded by the most recent device.
The breakthrough that enabled them to achieve a four-level system was the ability to manipulate and couple OAM and spin.
The major experimental accomplishment of the team's work was the inability to control all these parameters at once.
Think of the quantum states of our photon as planets on top of each other. We only knew about these planets' latitude. We could make a maximum of two levels of superposition. There was not enough information to put them into four. We also have latitude. This is the information that needs to be manipulated in a coupled way. We are holding the two planets in relation to each other.
Bob and Eve had quantum cryptography.
Superposition is used as a seal. The security of a communications channel is tested by sending randomly generated quantum states between sender and receiver.
If someone attempts to intercept a message, the sender and receiver are aware of it. If the transmission is mostly intact, Alice and Bob are able to use the quantum transmission as a key for secure communication.
Can this improve non-quantum communication security? If we imagine a photon as a sphere rotating upwards, we can get a rough idea of what a photon would look like in a certain way. We understand zero if we imagine it rotating downward.
Eve the eavesdropper can steal and replace classical photons when Alice or Bob send them. Even if Eve can't decode the data she has stolen, she may keep it for a long time.
Security is strengthened by quantum communication. We get an idea of how a qubit maintains its quantum state if we imagine the photon as a sphere rotating upwards and downwards at the same time.
Eve's ability to capture information will be compromised when she tries to steal and replace the qubit. Alice and Bob won't use a security key until they can prove that Eve didn't intercept it. The qubit key will be used in order to send the data.
Eve may be able to disturb the quantum channel despite the laws of quantum physics. Alice and Bob will need to keep sending keys until she stops interfering. The photon travels through space and causes interference patterns.
The information space of a qubit has a low tolerance for errors.
Additional dimensions are required to solve these problems. Imagine a photon rotating around the sun and the earth spinning in two different directions at the same time.
Eve won't be able to get any information if she tries to steal and replace the qudit. Eve's interference and accidental flaws introduced as the message travels through space will have a greater tolerance for error. Information will be securely exchanged between Alice and Bob.
"There is a lot of worry that mathematical encryption will become less and less effective because of the rapid advancement of computing technologies." Physical barriers make quantum communication impervious to future threats. We need to continue to develop and refine quantum communication technologies.
The Spin–orbit microlaser emits in a four-dimensional Hilbert space.
Journal information: Nature