
The PuTTY networking utility is being pushed by hackers with connections to the North Korean government in an attempt to back up their data, according to researchers.
Mandiant researchers said on Thursday that a customer had an employee install a fake network utility by mistake. The employer became a victim of the Airdry.v2 back door. The file was transmitted by someone.
According to company researchers, Mandiant identified several overlaps between UNC4034 and the threat clusters. The AIRDRY.V2 C2 URLs were previously used by these groups.
The threat actors were posing as people looking to hire. A file named Amazon_assessment.iso was sent to the target by the sender. ISO files have become more popular in recent months due to the fact that double-clicking on them causes them to become a virtual machine. The PuTTY.dll file was included in the image.
PuTTY is a secure application. It is signed by the developer. There was a version that was not signed.
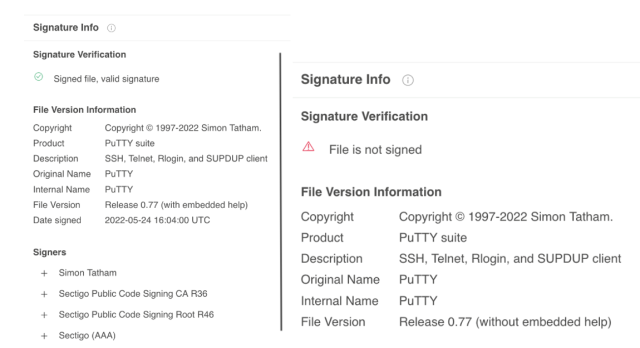
The US government believes that the North Korean government is behind the latest version of Airdry. A description of the US Cybersecurity and Infrastructure Security Agency can be found here. The Japanese community emergency response team has a description of the back door.