
Researchers have discovered a new type of malicious software that has been used by North Korea to read and download email from users' accounts.
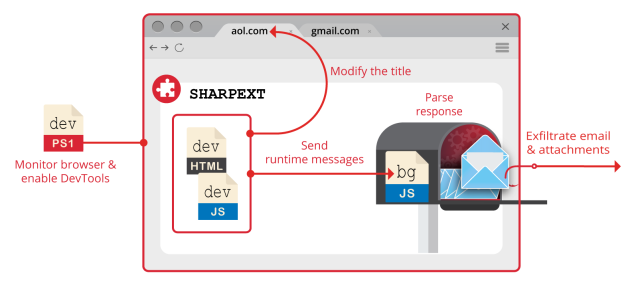
SHARPEXT is a browser extension that can be installed on the Chrome and Edge browsers, according to a report by Volexity. The extension can't be detected by the email services, and since the browser has already beenauthenticated, this increasingly popular security measure plays no role in reining in the account compromise. The extension is not available in the Chrome Web Store, Microsoft's add-ons page, or any other third party source.
The malware has been in use for "well over a year," Volexity said, and is the work of a hacking group the company tracks as SharpTongue. The group is sponsored by North Korea's government and overlaps with a group tracked as Kimsuky by other researchers. SHARPEXT is targeting organizations in the US, Europe, and South Korea that work on nuclear weapons and other issues North Korea deems important to its national security.Steven Adair, president of Volexity, said in an email that the extension gets installed by way of spearphishing and social engineering where the victim is fooled into opening a malicious document. In the past, threat actors from the Democratic People's Republic of Korea have launched spear-phishing attacks that were designed to get the victim to install a browser extension in order to steal their data. In the current incarnation of the software, it only works on Windows, but there's no reason why it can't be spread to other platforms.
AdvertisementThe logs obtained by Volexity show that the attacker was able to steal thousands of emails from multiple victims through the extension.
It's difficult to install a browser extension without the end- user noticing. SHARPEXT developers have paid attention to the research that shows how a security mechanism in the Chromium browser engine prevents malware from changing user settings. When a legitimate change is made, the browser takes a speach of the code to verify it. The browser asks for the old settings to be restored if any of them don't match.
The attackers need to get the following from the computer they're compromising to work around this protection.
After modifying the preference files, SHARPEXT loads the extension and executes a script that allows the browser to run custom code and settings.
The script checks for processes associated with the targeted browsers. If any targeted browsers are found running, the script checks the title of the tab for a specific phrase. When an active tab changes or a page is loaded, the malicious extension inserts a specific phrase into the title.
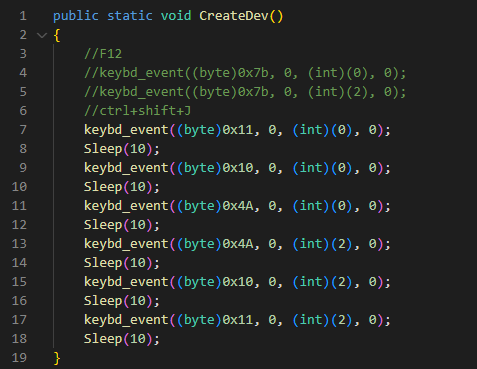
The post didn't stop.
AdvertisementThe keystrokes sent are equivalent to
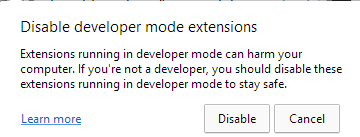
Control+Shift+J, the shortcut to enable the DevTools panel. Lastly, the PowerShell script hides the newly opened DevTools window by using the ShowWindow() API and theSW_HIDEflag. At the end of this process, DevTools is enabled on the active tab, but the window is hidden.In addition, this script is used to hide any windows that could alert the victim. Microsoft Edge, for example, periodically displays a warning message to the user (Figure 5) if extensions are running in developer mode. The script constantly checks if this window appears and hides it by using the
ShowWindow()and theSW_HIDEflag.
The extension can perform a number of requests after installation.
| HTTP POST Data | Description |
| mode=list | List previously collected email from the victim to ensure duplicates are not uploaded. This list is continuously updated as SHARPEXT executes. |
| mode=domain | List email domains with which the victim has previously communicated. This list is continuously updated as SHARPEXT executes. |
| mode=black | Collect a blacklist of email senders that should be ignored when collecting email from the victim. |
| mode=newD&d=[data] | Add a domain to the list of all domains viewed by the victim. |
| mode=attach&name=[data]&idx=[data]&body=[data] | Upload a new attachment to the remote server. |
| mode=new&mid=[data]&mbody=[data] | Upload Gmail data to the remote server. |
| mode=attlist | Commented by the attacker; receive an attachments list to be exfiltrated. |
| mode=new_aol&mid=[data]&mbody=[data] | Upload AOL data to the remote server. |
The hacker can create lists of email addresses to ignore and keep track of stolen email.
The following summary was created by Volexity.
After this post went live, a spokesman for the company said that the extension wasn't hosted on the company's server and that it was installed as a post-exploit software.
Using security hardened operating systems like ChromeOS is one of the best ways to prevent this type of attack.
Trained people can use the images, file names, and other indicators provided in the post to determine if they have been targeted or if they have been exposed to the malicious software. The company warned that the threat it poses isn't likely to go away anytime soon.
The tool seemed to be immature when Volexity first encountered it. The attacker is achieving its goals with the latest updates and ongoing maintenance.