Every account should give you the option to use two-factorAuthentication. Regardless of who you are, you should want your accounts to be as secure as possible. It doesn't matter which phone you use, 2FA will work with it. You have heard all of this before.
Two-factor methods are not the same as one another. The most secure methods of 2FA are the least convenient because of the tradeoff of convenience for protection. The least secure methods are the ones that are easiest to use.
We're going to discuss the pros and cons of each of the different ways you can use two-factor authentication on your device.
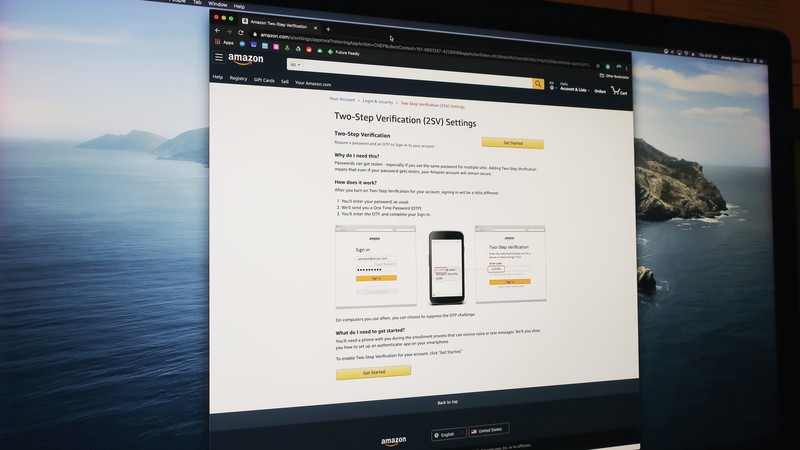
A text message with a two-factor code is one of the most popular ways to secure an online account. It is the worst way.
RECOMMENDED VIDEOS FOR YOU...
SMS-based 2FA is easy and convenient. It's also not very secure.
When you sign up for an account, you need to give your phone number. After the number is verified, a code is sent to you whenever you need to prove you are really you. Many companies offer it as the only way to secure an account because it's easy and convenient.
The ease of use and convenience are great, but nothing else is better than a text message. It wasn't designed to be a secure way of communication. Since it's an industry standard, even an app that doesn't offer secure messaging still sends plain text. Nathan is a senior analyst at Malwarebytes.
Text messages can be intercepted during transit. It is possible to send a message to the wrong phone number. There is no notification when a message reaches the correct number.
A bigger problem is that carriers can use someone else's phone number to authorize a new sim card. If someone really wanted to get access to your bank account or order a bunch of stuff from Amazon, all they need to do is convince someone at your carrier that they're you, you lost your phone, and you need your number moved to a new sim card
All of this is applicable for email-based verification. Email is the only way any account recovery process can work, and a lot of places will want to send you a code via email to log in from a new device. Everyone in the industry is aware that it is not very secure. It's possible that fixing how email is used for this sort of thing is the next step.
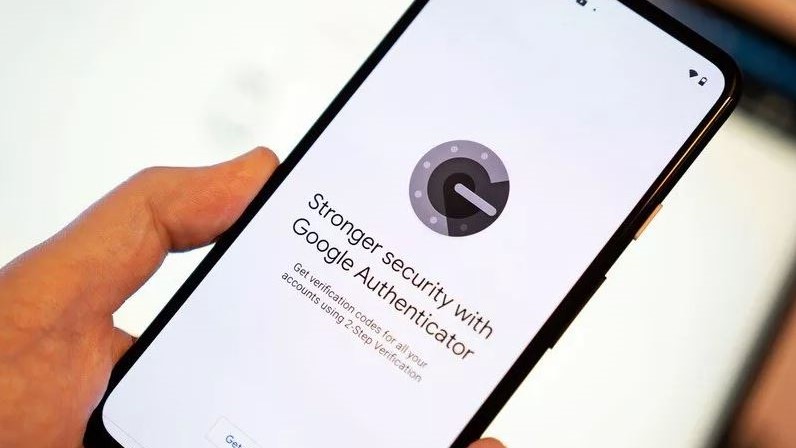
There is a significant improvement over 2FA. They use Time-Based One Time Passwords (TOTP) that an application on your phone can create using a complex algorithm without a network connection. The same program is used to make sure the code is right.
Authenticator apps are better than SMS for 2FA, but they are not foolproof.
Since they work offline, TOTP style 2FA is not subject to the same problems as using SMS, but it does have its own set of flaws. It is not easy to intercept and manipulate the data you send when you enter the TOTP on a website.
Phishing is the real issue. It's possible to create a fake website that looks and acts like the real thing, and even pass along your credentials, like your password and TOTP, to log in to the real service. It logs in at the same time and can act as if you're not using the service at all. Proper credentials were provided.
It might be difficult to get the codes if you lose your phone. Authy is an authenticator app that uses a central password to get things up and running quickly.
Most companies will give you a set of backup codes for when things go wrong. The effectiveness of using TOTP is weakened by the fact that data is being sent across the internet.
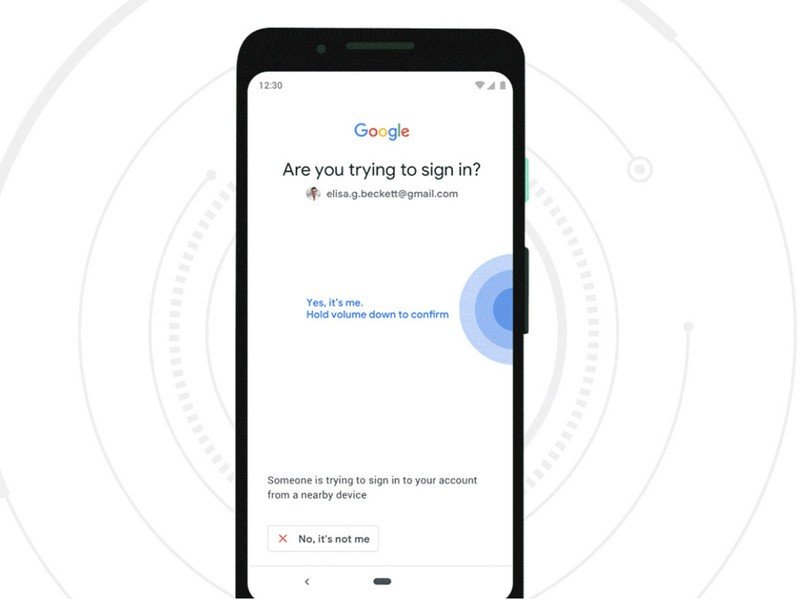
A prompt can be sent to your phone when you try to log in to a service. The prompt tells you that someone is trying to log into your account, that they can give an approximate location, and that you can either approve or deny it. You just tap a button if it's you.
A notification for 2FA is super easy and super convenient. Don't lose your phone, though.
2FA is improved by push-based 2FA. It all works through a standard notification on your phone, so you don't have to do anything. It has shown to be very resistant to hacking. It's never a good idea to say never.
Some of the disadvantages of TOTP are that you have to be online through a data connection and you have to hold the right device to get the message. You can't always use a login prompt for your other accounts because it is not very standardized.
Push-based 2FA is convenient and secure. It's going to be a factor in the future of 2FA for your account.

An authenticator device or a U2F security key can be used to secure an online account. I can tell you that it's not very popular because it's the way I use.
If you want to log in from a new device or after an amount of time set by an account administrator, you need to have the same device.
The device sends a signed challenge code to the server that is specific to the site, your account, and the device itself. U2F has been hack-proof. Don't say never again.
Using a U2F key is the least convenient but most secure way to do two-factor authentication. It's probably not for you because it's a huge PITA.
It is possible to set up more than one device on the same account, so you won't lose access if you lose your security key, but it still means that you need to have that key with you every time you log in to a website or service.
If I use a U2F key, I need to give the key every 12 hours to get back into my work account. I have a key in my desk drawer and a friend keeps an envelope for me in the event of an emergency.
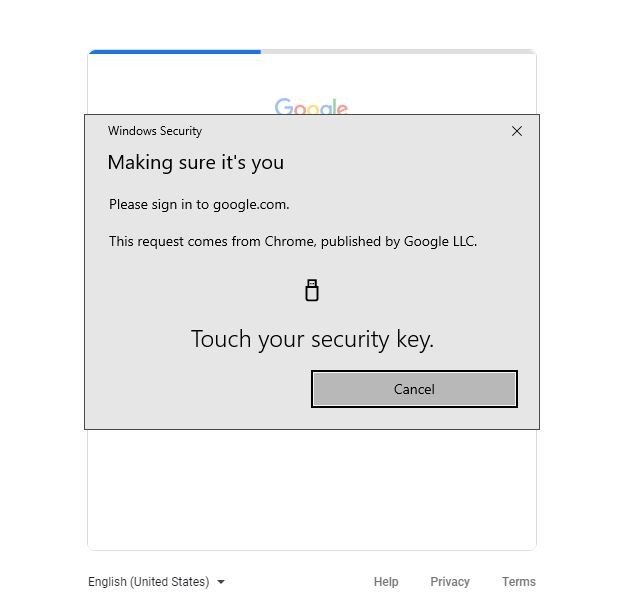
It is possible to set up a backup method of 2FA if you use a key. It's great for convenience, but it also compromises the security of your account because the less secure methods are still viable.
Cost is one of the drawbacks to using a hardware token. It's free to use an authenticator app or push-based 2FA. You will need to purchase a security key in order to use it. This can add up if you have at least one backup key.
It's difficult to use a security key with your phone. No method is 100% reliable when it comes to using a key with a phone.
None of them.
Any type of 2FA on an account is better than none at all, and evenSMS-based 2FA means you're more protected than you would be if you just relied on a password. If you have the patience, you can use a program like the Advanced Protection Program. You have to consider convenience against security.
Even I can hack 2FA, so I wish it wouldn't happen. If you're willing to do a little bit of reading and copying, you can. It means that anyone can hack it, and there are people out there that will take a lot of time and effort to try it on someone.
Even though you aren't a politician or a movie star, you are still a target for online hackers. You need to protect your online accounts by taking the extra steps. Knowing more about the different methods of two-factor authentication can help you make the right decision.