According to new research, security vulnerabilities in a popular Chinese-built gps vehicle tracker can be easily exploited to cut the engines of a million vehicles around the world. The company that makes the tracker didn't bother to fix them.
Micodus, a Shenzhen-based electronics maker, claims to have built more than 1.5 million hardwiredGPS trackers in use today across more than 420,000 customers. Fortune 50 companies, as well as a nuclear power plant operator, were found by Bit Sight.
The security flaws can be used to track any vehicle in real-time, access past routes, and cut the engines of vehicles.
The vulnerabilities are not difficult to exploit, and the nature of the flaws leaves significant questions about the vulnerability of other models, according to the report written by Pedro Umbelino.
The severity of the bugs and the fact that there are no fixes made it necessary for car owners to remove the devices.
All but one of the vulnerabilities is a high severity or greater. The web dashboard that customers use to track their vehicle fleets has some bugs in it.
A hardcoded password can be used to gain complete control of a gps tracker, access to vehicles real-time location and past routes, and remote cut off fuel to vehicles. Anyone can find the password by looking at the code of the app.
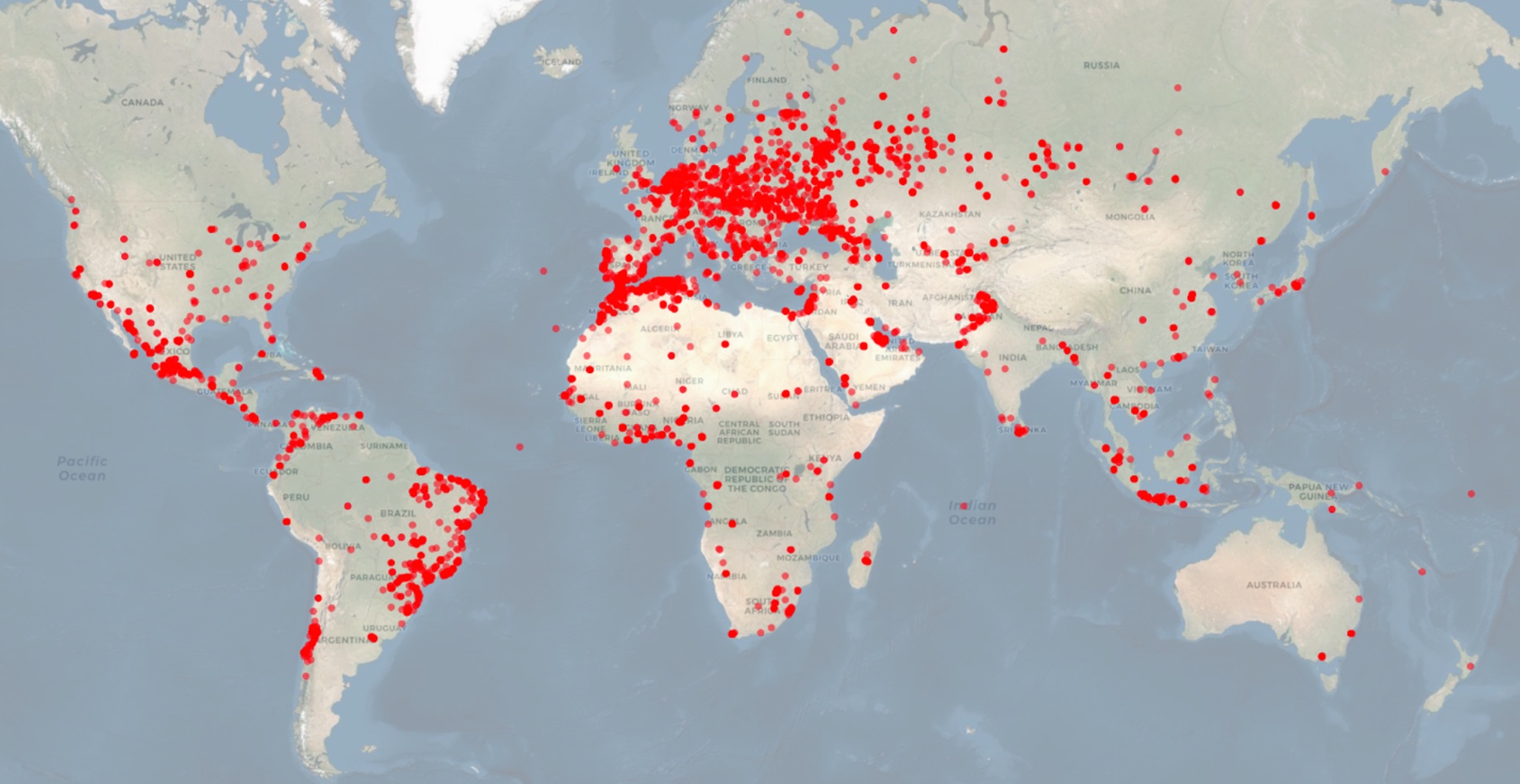
There is a map with points. The image was supplied by Bit Sight.
The research shows that the default password for the gps tracker is "123456", which makes it easy for anyone to access it. 99% of a sample of 1,000 devices were accessible with an unchanged default password, likely because device owners aren't required to change the device's password on setup
Two of the remaining vulnerabilities, known as direct object references, allow a log-in user to access data from a vulnerable gps tracker that didn't belong to them, and generate spreadsheets containing device activity.
The highest concentration of vulnerable Micodus devices were found in Ukraine, Russia, Uzbekistan, and Brazil, as well as in Spain, Poland, Germany and France. According to Kevin Long, a spokesman for BitSight, there is a smaller percentage of devices in the United States.
Stephen Harvey said the vulnerabilities could result in disastrous consequences for vehicle owners. The vulnerabilities were not fixed before the report was published, despite the security company contacting Micodus. Companies are usually given three months to fix vulnerabilities before they are made public by security researchers.
Micodus did not reply before the publication.
Flaws in third-party software exposed dozens of Teslas to remote access