An industrial control engineer inadvertently made a workstations part of a botnet after installing a piece of software that was meant to recover lost passwords.
Passwords are lost in a lot of organizations. A controller used to automate processes in factories, electric plants, and other industrial settings may be set up and forgotten over time. A replacement engineer can discover that the original engineer never left the password behind before leaving the company.
According to a post on a security firm's website, an entire system of malicious software tries to exploit scenarios like this inside industrial facilities. Password crackers are the workhorses inside these environments and are promoted in online ads.
A customer's system had run software that was able to recover the password for the DirectLogic06, a PLC sold by the company. The software was able to recover the password, but not through normal methods. The software was able to exploit a zero-day vulnerability in Automatic DirectPLCs.
Advertisement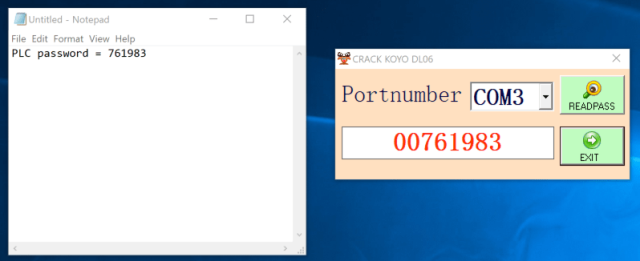
Sam Hanson wrote that previous research had led to successful cracking techniques. A scrambled version of the password is not cracked by this exploit. A specificbyte sequence is sent to a COM port.

The vulnerability and a related one found by Hanson have been patched. The severity of the vulnerability was raised to 7.5 out of a possible 10.
The software was installed on the customer's network to recover the password. It made the system part of a botnet and monitored the clipboard of the workstations that were part of it.
The hijacker replaces the address with one owned by the threat actor. The in-real-time hijacking is an effective way to steal from users who want to transfer funds and increase our confidence that the adversary is financially motivated.
Hanson said that he has found password crackers for a wide range of industrial software sold by other companies. They are included.
| Vendor and Asset | System Type |
| Automation Direct DirectLogic 06 | PLC |
| Omron CP1H | PLC |
| Omron C200HX | PLC |
| Omron C200H | PLC |
| Omron CPM2* | PLC |
| Omron CPM1A | PLC |
| Omron CQM1H | PLC |
| Siemens S7-200 | PLC |
| Siemens S7-200 | Project File (*.mwp) |
| Siemens LOGO! 0AB6 | PLC |
| ABB Codesys | Project File (*.pro) |
| Delta Automation DVP, ES, EX, SS2, EC Series | PLC |
| Fuji Electric POD UG | HMI |
| Fuji Electric Hakko | HMI |
| Mitsubishi Electric FX Series (3U and 3G) | PLC |
| Mitsubishi Electric Q02 Series | PLC |
| Mitsubishi Electric GT 1020 Series | HMI |
| Mitsubishi Electric GOT F930 | HMI |
| Mitsubishi Electric GOT F940 | HMI |
| Mitsubishi Electric GOT 1055 | HMI |
| Pro-Face GP Pro-Face | HMI |
| Pro-Face GP | Project File (*.prw) |
| Vigor VB | PLC |
| Vigor VH | PLC |
| Weintek | HMI |
| Allen Bradley MicroLogix 1000 | PLC |
| Panasonic NAIS F P0 | PLC |
| Fatek FBe and FBs Series | PLC |
| IDEC Corporation HG2S-FF | HMI |
| LG K80S | PLC |
| LG K120S | PLC |
An analysis of a few samples indicated that they also contained some kind of malicious software.
According to Hanson, there is an environment for this kind of software. Several websites and multiple social media accounts have passwords that are known ascrackers.
The account shows the carelessness that still operates in many industrial control settings. There is no reason why more malicious hackers out to sabotage a dam, power plant, or similar facility wouldn't do the same thing.