
Microsoft detailed an ongoing large-scalePhishing campaign that can hijack user accounts when they're protected with multi-factorAuthentication measures designed to prevent such takeovers. The threat actors behind the operation have been able to trick employees into sending them money by using victim email accounts.
The gold standard for account security is multi-factor verification. It requires the account user to prove their identity with something they own or control, as well as something they know, in addition to something they own. Attacks have found ways to respond to the growing use of MFA.
An attacker-controlled proxy site was put between the account users and the work server they tried to log into. The proxy site sent the password to the real server after the user entered it into the site. The user doesn't need to be reauthenticated every time they visit a new page because the threat actor stole the session cookie. The campaign started with a phish email with an attachment.
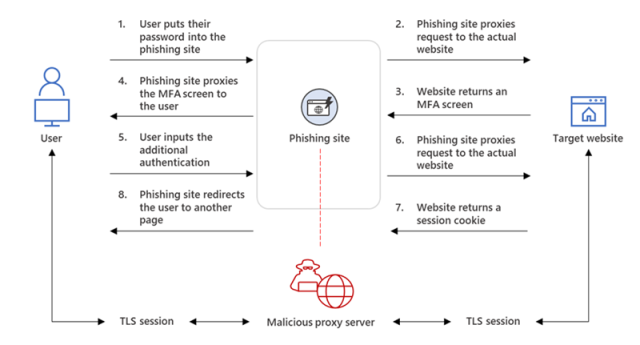
The attackers used the stolen session cookie to sign up for Outlook online, according to members of the Microsoft Threat Intelligence Center. The attacker used the session cookie to gain access to the compromised account even if the organization had anMFA policy.
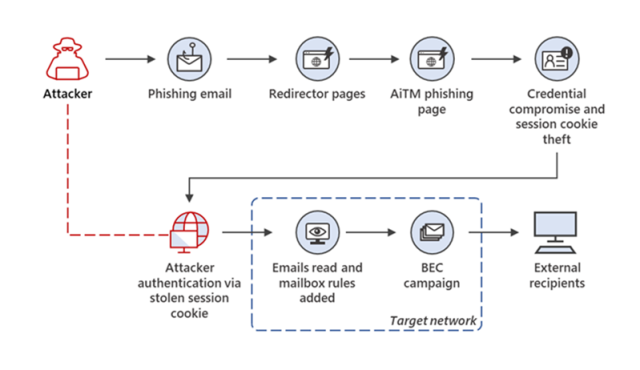
The threat actors accessed employee email accounts and looked for messages to use in business email compromise scam, which tricked targets into wiring large sums of money to accounts they believed belonged to co-workers or business partners. The attackers tricked the other party into making a payment by using the hacked employee's forged identity.
AdvertisementThe threat actors created inbox rules that moved specific emails to an archive folder and marked them as read to prevent the employee from discovering the compromise. The threat actor was constantly checking for new emails.
The attackers conducted multiple fraud attempts from the same mailbox. When an attacker finds a new fraud target, they update the Inbox rule they created to include the new targets' organization domain.
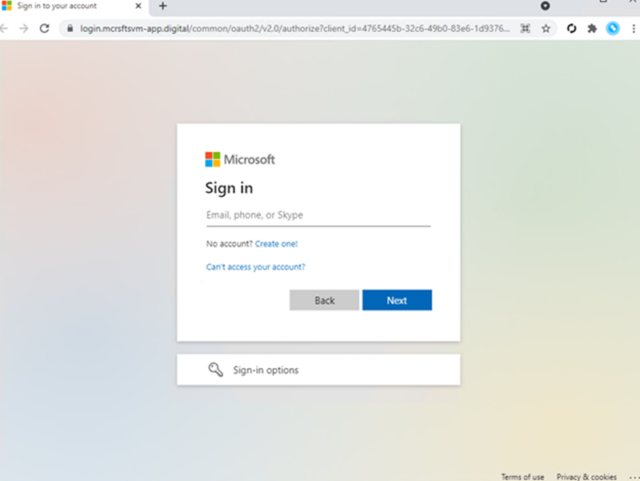
The post shows how easy it is for an employee to fall for a scam. It's difficult to know when a message is authentic because of the volume of emails. Good security hygiene is signaled by the use of MFA. The proxy site landing page is one of the few visually suspicious parts of the scam. Even though most organization specific login pages are opaque, the domain name may still be a clue.
In Microsoft's account, nothing should be said that deployment of MFA isn't one of the best ways to prevent account takeovers. Some MFA is better than others. Even though one-time verification codes are better than nothing, they are still phishable and can be used for other purposes.
The most effective forms of MFA available are those that are compliant with standards set by the industry-wide FIDO Alliance. These types of MFA use a physical security key that can come as a dongle from companies like Yubico or Feitian or even an Android or iOS device. The authentication can also come from a fingerprint or retina scan, neither of which ever leave the end-user device to prevent the biometrics from being stolen. What all FIDO-compatible MFA has in common is that it can't be phished and uses back-end systems resistant to this type of ongoing campaign.