
Researchers reported on Tuesday that an advanced hacking group has spent almost two years infecting a wide range of routers in North America and Europe and taking full control of connected devices.
Researchers from Black Lotus Labs say they've identified at least 80 targets that have been affected by the stealthy software. ZuoRAT is part of a larger hacking campaign that has existed since at least the fourth quarter of 2020.
Given its range of capabilities, the discovery of custom-built malicious software written for the MIPS architecture is significant. The hallmark of a highly sophisticated threat actor is its ability to enumerate all devices connected to aninfecting router and collect the network traffic it sends and receives.
Black Lotus Labs researchers wrote that it is not a novel technique to compromise a SOHO routers to gain access to an adjacentLAN. Reports of person-in-the-middle style attacks are rare and mark of a complex and targeted operation. A high level of sophistication by a threat actor was demonstrated by the use of these two techniques.
The campaign comprises at least four pieces of malware, three of them written from scratch by the threat actor. The first piece is the MIPS-based ZuoRAT, which closely resembles the Mirai Internet of Things malware that achieved record-breaking distributed denial-of-service attacks that crippled some Internet services for days. ZuoRAT often gets installed by exploiting unpatched vulnerabilities in SOHO devices.ZuoRAT enumerates the devices that are connected to the internet. The threat actor can cause the connected devices to install other malicious software. Two of the pieces are custom-made, the first for Windows and the second for Linux and macOS. ZuoRAT can be used to hack connected devices.
Advertisement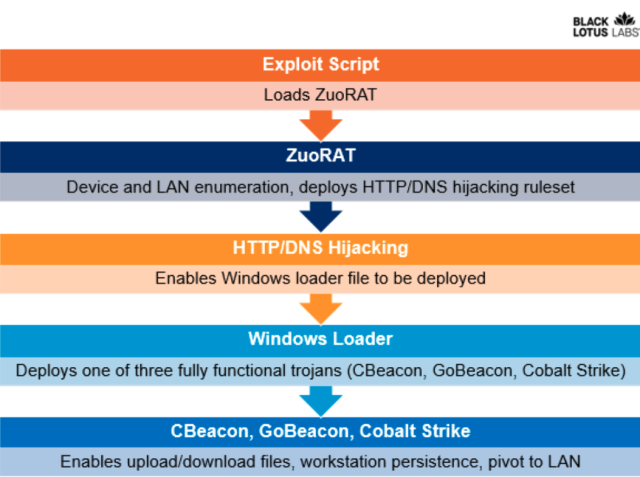
ZuoRAT can pivot infections using either method.
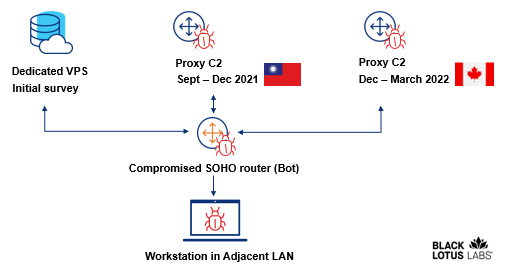
The command and control infrastructure used in the campaign is complex in order to hide what's happening. One set of infrastructure is used to control the routers, and the other is reserved for the connected devices if they are later affected by the disease.
The researchers observed a persistent connection to a control server that they believe was being used to conduct an initial survey on the targets. Some of the 23 routers interacted with a Taiwan-based proxy server. The attacker's infrastructure was obfuscated by a subset of the routers.
The steps are shown in this graphic.
The landing page of a control server was disguise by the threat actors.
The researchers had written.
AdvertisementThe discovery of this ongoing campaign is the most important one affecting SOHO routers since VPNFilter, the router malware created and deployed by the Russian government that was discovered in 2018. Routers are often overlooked, particularly in the work-from-home era. While organizations often have strict requirements for what devices are allowed to connect, few mandate patching or other safeguards for the devices' routers.Black Lotus Labs visibility indicates ZuoRAT and the correlated activity represent a highly targeted campaign against US and Western European organizations that blends in with typical internet traffic through obfuscated, multistage C2 infrastructure, likely aligned with multiple phases of the malware infection. The extent to which the actors take pains to hide the C2 infrastructure cannot be overstated. First, to avoid suspicion, they handed off the initial exploit from a dedicated virtual private server (VPS) that hosted benign content. Next, they leveraged routers as proxy C2s that hid in plain sight through router-to-router communication to further avoid detection. And finally, they rotated proxy routers periodically to avoid detection.
ZuoRAT can not survive a restart. The ZuoRAT exploit consists of files that are stored in a temporary directory. Factory resets are the best way to fully recover from infections. In the event that connected devices have been exposed to the other malware, they can't be wiped clean.