
Last year, the company issued an update that made it easier to start its cars. The feature can be used to steal cars.
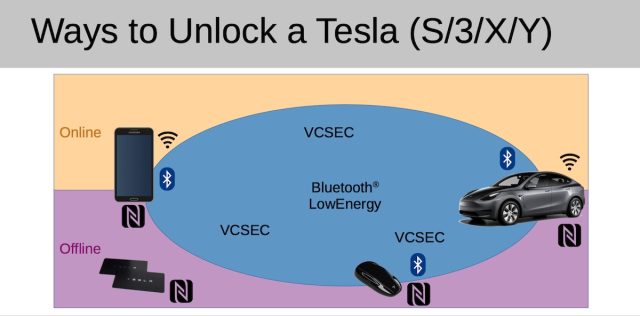
For a long time, drivers had to put their key card on the center console in order to start driving. Drivers were able to operate their cars immediately after they unlocked them with the update. One of the ways to get into a car is by using a phone app, a key or a card.
Martin Herfurt, a security researcher in Austria, noticed something odd about the new feature: Not only did it allow the car to start within 130 seconds of being unlocked, but it also put the car in a state to accept entirely new keys.
Herfurt said in an online interview that the 130-second interval authorization is too general. The use of the card as a primary means of using the car has been made easier by the introduction of this timer. It should be possible to start the car without the user having to use the key again. Within the 130-second period, not only the driving of the car is authorized, but also the rolling of a new key is a problem.
AdvertisementEven though the official phone app doesn't allow keys to be Enrolled unless they are connected to the owner's account, Herfurt was able to exchange messages with any nearby BLE device. The researcher built his own app that uses the same language that the officialTesla app uses.
A malicious version ofTeslakee that Herfurt designed for proof-of-concept purposes shows how easy it is for thieves to steal someone's key. A benign version ofTeslakee will be released eventually that will make such attacks harder to carry out. The attacker uses theTeslakee app to send and receive VC Sec messages.
All you have to do is be within range of the car during the crucial 130-second window when it will be unlocked. The attacker can block the BLE frequencies used by the phone-as-a-key app by using a signal jamming device.
The video shows the attack in motion.
The thief began exchanging messages with the car after the driver unlocked the car with an Near Field Communication card. The messages give the thief a key to the car before the driver leaves. The thief can use the key to get into the car. There is no indication from the in-car display that something isn't right.
He hasn't tested the method on the new models, but he thinks they are vulnerable because they use the same native support for phone-as-a-key.
An email was sent toTesla seeking comment on the post.