A new vulnerability in Microsoft Office could allow someone to take control of your computer. Even if you don't open a file, the vulnerability can be exploited.
If you use Microsoft Office frequently, be sure to check out the workaround Microsoft has released for this exploit.
Interesting maldoc was submitted from Belarus. It uses Word's external link to load the HTML and then uses the "ms-msdt" scheme to execute PowerShell code.https://t.co/hTdAfHOUx3 pic.twitter.com/rVSb02ZTwt
— nao_sec (@nao_sec) May 27, 2022
The vulnerability has been dubbed Follina by one of the researchers who first looked into it. On May 27th, it came to light through a statement by nao_sec, who said that Microsoft first heard of it in April. The exploit gets entry into the attacked computer by disabling the Microsoft Support Diagnostic Tool.
The exploit affects only.rtf files, but other files can also be affected. The program can be loaded and executed from external sources with the help of a feature in Word. Follina uses this in order to enter the computer and then runs a series of commands that opens up the computer. Microsoft uses a safe tool called the Microsoft Severity Detection Toolkit to investigate various issues for Windows users. It grants remote access to your computer, which helps the exploit take control of it.
The exploit can run even if you don't open the file. Follina can be executed if you view it in File Explorer. Once the attacker gains control of your computer, it's up to them to do what they want. They might download malicious software, leak files, and do a lot of other things.
There are many examples of how Follina has been exploited in various files. The exploit is being used for other things. You don't want this on your computer.
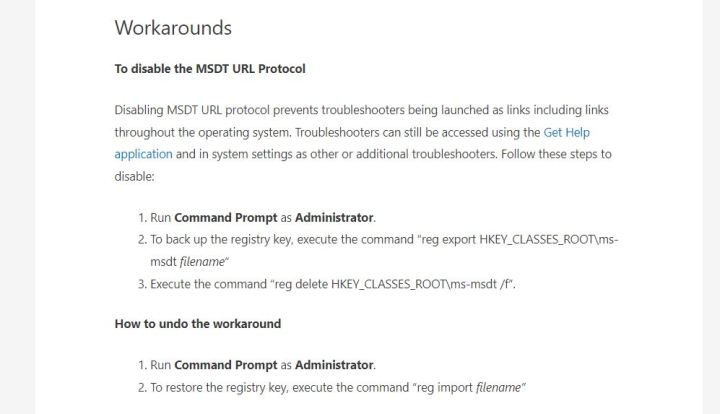
There are a few things you can do to stay safe from the Follina exploit until Microsoft releases a patch. The official fix is the workaround, and we don't know if anything else will follow.
Check to see if your version of Microsoft Office could be affected. The vulnerability has been found in several Office products. It's better to take additional precautions because there is no guarantee that older versions of Microsoft Office are safe.
It's not a bad idea to avoid using.doc,.docx, and.rtf files for the time being. Consider using cloud-based alternatives. It's a good idea to only accept and download files from 100%-proven sources.
Follow Microsoft's guidance on disabling MSDT. It requires you to open the Command Prompt and run it as administrator, then input a couple of entries. You should be safe from Follina if everything goes according to plan. Remember to always be cautious.
Recommended video