
For more than a decade, we have been promised that a world without passwords is just around the corner, and yet year after year, this security nirvana proves out of reach. For the first time, a form of passwordless authentication is about to become available to the public in the form of a standard that allows for cross-platform and cross-service passkeys.
Password-killing schemes had a number of problems. There was a lack of a viable recovery mechanism when someone lost control of their phone numbers. Most solutions failed to be passwordless. Instead, they gave users options to log in with a face scanning or fingerprints, but these systems ultimately fell back on a password, and that's why we hated passwords in the first place.
This time, Apple, Microsoft, and Google all seem to agree on a solution. The solution is easier for users and less expensive for big services like Facebook to roll out. It has been peer-reviewed by experts in security.
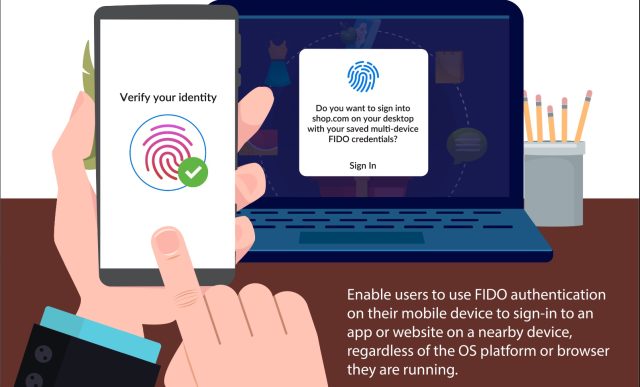
Over the past five years, the current multifactor authentication methods have made important strides. When logging in to my account from a new device, I use an app downloaded from the App Store or the Play Store as a second factor. The system uses a protocol called CTAP, short for client to authenticator, to make sure that the phone is in proximity to the new device and that it is connected to the internet. That means it is unphishable. The standard makes sure that the secret on the phone can't be accessed.
AdvertisementThe Advanced Protection Program requires physical keys in the form of end-user phones or dongles to be used toauthenticate logins from new devices.
The biggest limitation is that each service provider has their own way of rolling out passwordless and MFA. Most banks and financial services still send one-time passwords via email or text. To allow the addition of a second factor, many services have moved on to a method known as TOTP, short for time-based one-time password.
Physical security keys, TOTPs, and to a lesser extent two-factor authentication through SMS and email represent an important step forward, but there remain three key limitations. First, TOTPs generated through authenticator apps and sent by text or email are phishable, the same way regular passwords are. Second, each service has its own closed MFA platform. That means that even when using unphishable forms of MFA—such as standalone physical keys or phone-based keys—a user needs a separate key for Google, Microsoft, and every other Internet property. To make matters worse, each OS platform has differing mechanisms for implementing MFA.The sheer unusability for most end users and the nontrivial cost and complexity each service faces when trying to offer MFA give way to a third problem.