
It isn't the kind of security discovery that happens often. A previously unknown hacker group used a novel backdoor, top-notch trade craft, and software engineering to create an espionage botnet that was largely invisible in many victim networks.
The group, which security firm Mandiant is calling UNC3524, has spent the past 18 months burrowing into victims. When a group is ejected, it takes no time to re-invade the victim environment and pick up where things left off. There are many keys to its stealth.
In a post, Mandiant researchers wrote:
Throughout their operations, the threat actor demonstrated sophisticated operational security that we see only a small number of threat actors demonstrate. The threat actor evaded detection by operating from devices in the victim environment’s blind spots, including servers running uncommon versions of Linux and network appliances running opaque OSes. These devices and appliances were running versions of operating systems that were unsupported by agent-based security tools, and often had an expected level of network traffic that allowed the attackers to blend in. The threat actor’s use of the QUIETEXIT tunneler allowed them to largely live off the land, without the need to bring in additional tools, further reducing the opportunity for detection. This allowed UNC3524 to remain undetected in victim environments for, in some cases, upwards of 18 months.
The SOCKS tunnel allowed the hackers to effectively connect their control server into a victim's network where they could execute tools without leaving traces on any of the victim computers.
Advertisement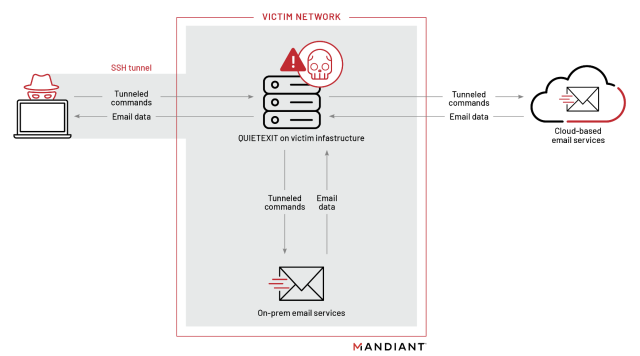
An alternate means of access was provided by a secondary back door. It was based on a version of the reGeorg webshell that was heavily obfuscated to make it harder to detect. The threat actor used it if the primary backdoor stopped working. The researchers had more to say.
Once inside the victim environment, the threat actor spent time to identify web servers in the victim environment and ensure they found one that was Internet accessible before copying REGEORG to it. They also took care to name the file so that it blended in with the application running on the compromised server. Mandiant also observed instances where UNC3452 used timestomping [referring to a tool available here for deleting or modifying timestamp-related information on files] to alter the Standard Information timestamps of the REGEORG web shell to match other files in the same directory.
One of the ways the hackers maintain a low profile is by favoring standard Windows protocols. The tool that was used to establish a shell on the remote system was a custom version of Windows Management Instrumentation.
Quietexit's final goal is to obtain documents related to things like corporate development, mergers and acquisitions, and large financial transactions by accessing email accounts of executives and IT personnel.
After obtaining privileged credentials to the mail environment, they began making Exchange Web Services ( ) requests to either the on-premises Microsoft Exchange or Microsoft Exchange Online environment.